I have been toying around with the concept of a web fob. The concept is the same as a key fob, only it would be entirely web based. The primary benefit of this would be that you wouldn’t have to carry around a hardware security token in order to gain access to secure systems.
Here’s how it would work:
1. The user would navigate to an undisclosed site and log in, at which time a security token would be generated.
The user would know, most likely through site/network administrators, that they must go to another location to gather the security token. They would navigate to this undisclosed web site, enter their authentication information, and would be handed a token. This token could be a series of digits, a phrase, or even a file that the user downloads. The possibilities are really only limited by the imagination. The ways this token could be generated are numerous and are already a well solved problem with key fobs. The technique would likely be the same or very similar, only web based. The key to this would be in maintaining secrecy in how the security tokens are generated, meaning the processing would need to be done server side.
2. A user would attempt to gain access to the secure system and would be prompted for a security token to proceed.
This could be a website, VPN, or any other system. The only basic criteria is that authentication must include something more than a simple user name and password. The user would be greeted with the login page for the site which would display fields asking for username, password, whatever else is important, and the security token. This page would have no indication of where the security token should come from.
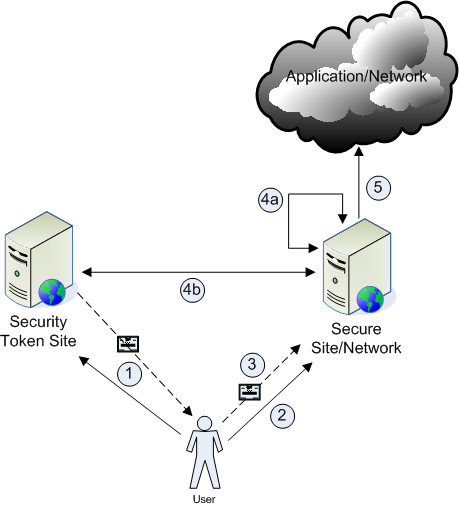
3. The token would be input into the site, along with login credentials.
Self explanatory.
4. The application would authenticate the token.
The application would either know how to authenticate the security token itself (4a) or would have a server side service that exposed a validation routine from the servers generating the security token (4b).
5. The user is granted access.
Assuming successful authentication, of course.
I know enough about security to ride the edge of chaos and mostly get away with it but by no means consider myself a guru. The main problem I see with this lies in the maintenance of the security token site and keeping it secure. So to all you security gurus: what do you think of this concept? Is it secure? Is there a benefit? Is it already being done somewhere (I couldn’t find one)?
